Share this
WannaCry: Global Ransomware Attack Slowed But NOT Stopped
by Bridget.Giacinto on May 15, 2017 11:53:25 AM

On Friday, May 12th an unprecedented cyber ransomware attack swept the globe. This ransomware, called WannaCry has, as of Monday, hit over 200,000 systems around the world, affecting more than 150 countries. At least 16 hospitals in England's National Health Services (NHS) were affected, completely locking nurses and doctors out of patients' health records. This is the most severe, wide-spread malware attack to date, and thanks to the swift actions of a 22-year old security researcher it has slowed … but not stopped.
What is WannaCry?
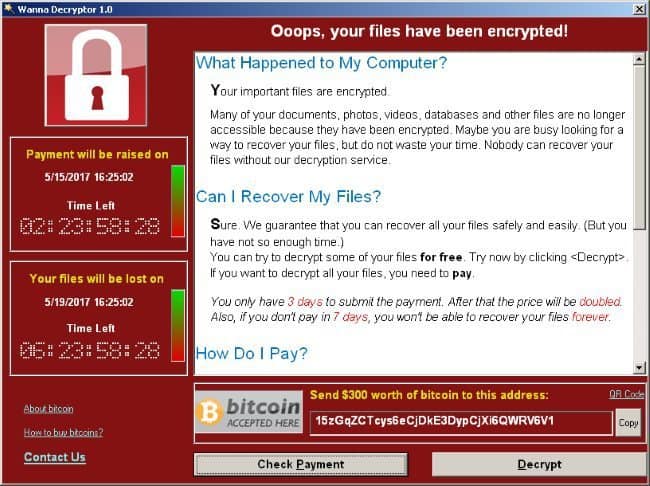
WannaCry is a malicious type of malware called Ransomware that encrypts files on your computer, requiring you to pay a ransom in order to decrypt or unlock your files. This ransomware is also known as WanaCryptor, WCry, WannaCry, WannaCrypt or Wanna Decryptor.
While Ransomware attacks have been on the rise over the last few years, this particular malware, is exploiting a security flaw in Microsoft Windows operating systems that was made public knowledge last month by a group of hackers called Shadow Brokers. While Microsoft already issued a security update to patch this vulnerability for supported operating systems, on Friday, in response to this outbreak, they issued another patch for older and unsupported operating systems.
According to Aleksandr Yampolskiy, CEO of SecurityScoreCard, "Companies should be on high alert. Millions of organizations across the globe are potentially vulnerable to this type of attack."
What Does WannaCry do Specifically?
If your computer is hit with a ransomware like WannaCry, your files will be encrypted rendering them useless. Without the decryption key, your files will no longer be accessible. Once your files have been encrypted, you will receive a notice on your computer demanding a ransom of $300 in bitcoin to be paid to the cyber criminals to receive a key to decrypt your files. After three days, the ransom doubles to $600. After 7 days, your files are deleted and all of your encrypted files are gone for good.
What do You Mean the WannaCry Attack is Not Over?
While the kill switch for the WannaCry virus was discovered by Marcus Hutchins, a 22-year-old security researcher, the attack is far from over. On Saturday, May 13th, the security researcher, whose job it is to track and try to stop botnets (and other kinds of malware) by picking up unregistered malware control server domains, discovered that WannaCry was using an unregistered domain in the code of their malware software. When he registered it, he unknowingly hit the malware kill switch.
How this works: When a computer is infected with WannaCry, the computer reaches out to a command and control center, which is controlled by the hacker. This allows the hacker to control what happens to the infected computer. By registering the malware control server domain, which was previously unregistered, and pointing the domain traffic to a sinkhole, Marcus Hutchins slowed the spread of the malware virus… at least temporarily. Unfortunately, all the hackers have to do is point the malware to a different command and control domain and the ransomware virus will pick up again.
How do Your Protect Yourself from WannaCry?
There are a few things you can do to protect yourself now, before this ransomware gains speed again.
- Apply the most recent Microsoft patch for Windows systems
- Make sure you have anti-virus software and keep it up-to-date
- Think before you click
- Don’t open attachments you are not sure about
- Back up your data using the 3-2-1 backup rule
Please note: Putting your data in the cloud does NOT leave you less vulnerable to this attack. Instead, you are dependent upon 3rd party providers and if one of them gets hacked, you are in trouble. Which is why you should not rely on cloud alone.
For more information on how to protect yourself from Ransomware, catch the recording of our Webinar on The Ransomware Attack You Weren’t Ready For.
To view our current webinars or our recorded webinars, visit our webinar page.
Share this
- Pre-Sales Questions (112)
- Tips and Tricks (95)
- Industry News (60)
- Reseller / MSP (37)
- Security Threats / Ransomware (29)
- Applications (28)
- Best Practices (26)
- Cloud Backup (25)
- Backup Videos (24)
- Disaster Recovery (24)
- Compliance / HIPAA (23)
- Storage Technology (21)
- Virtual Environments (17)
- Technology Updates / Releases (9)
- Infographics (8)
- Backup preparation (3)
- Company (US) (1)
- Events (1)
- Events (US) (1)
- Products (US) (1)
- March 2024 (2)
- February 2024 (2)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (1)
- July 2023 (1)
- May 2023 (1)
- March 2023 (3)
- February 2023 (2)
- January 2023 (3)
- December 2022 (1)
- November 2022 (2)
- October 2022 (2)
- September 2022 (2)
- August 2022 (2)
- July 2022 (1)
- June 2022 (1)
- April 2022 (1)
- March 2022 (2)
- February 2022 (1)
- January 2022 (1)
- December 2021 (1)
- November 2021 (1)
- September 2021 (1)
- August 2021 (1)
- July 2021 (1)
- June 2021 (2)
- May 2021 (2)
- April 2021 (1)
- March 2021 (2)
- February 2021 (1)
- January 2021 (2)
- December 2020 (1)
- November 2020 (1)
- October 2020 (2)
- September 2020 (4)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (1)
- March 2020 (3)
- February 2020 (2)
- January 2020 (2)
- December 2019 (1)
- November 2019 (1)
- October 2019 (1)
- August 2019 (1)
- July 2019 (1)
- June 2019 (1)
- April 2019 (1)
- February 2019 (1)
- January 2019 (1)
- December 2018 (1)
- November 2018 (2)
- August 2018 (3)
- July 2018 (4)
- June 2018 (2)
- April 2018 (2)
- March 2018 (2)
- February 2018 (2)
- January 2018 (3)
- December 2017 (1)
- September 2017 (1)
- May 2017 (2)
- April 2017 (5)
- March 2017 (4)
- February 2017 (1)
- January 2017 (1)
- December 2016 (1)
- November 2016 (1)
- October 2016 (2)
- September 2016 (1)
- August 2016 (3)
- July 2016 (2)
- June 2016 (3)
- May 2016 (7)
- April 2016 (8)
- March 2016 (1)
- February 2016 (3)
- January 2016 (12)
- December 2015 (7)
- November 2015 (6)
- October 2015 (6)
- September 2015 (2)
- August 2015 (4)
- July 2015 (2)
- June 2015 (2)
- May 2015 (1)
- April 2015 (5)
- March 2015 (3)
- February 2015 (4)
- January 2015 (2)
- October 2014 (5)
- September 2014 (8)
- August 2014 (5)
- July 2014 (8)
- June 2014 (5)
- May 2014 (5)
- April 2014 (9)
- March 2014 (7)
- February 2014 (7)
- January 2014 (5)
- December 2013 (5)
- October 2013 (7)
- September 2013 (2)